Cybersecurity
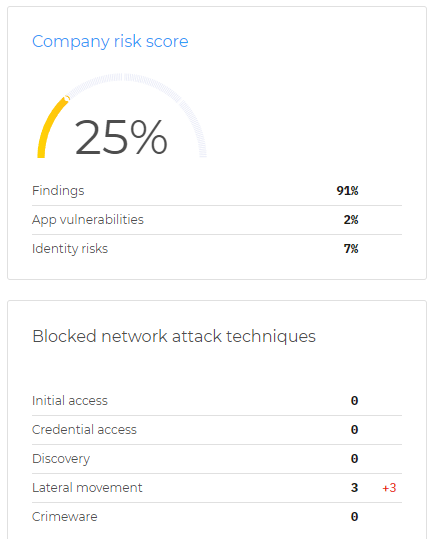
Cybersecurity threats are always changing, but so are our defences. We helped protect your network and cloud environments with services that prevent, detect, and respond to attacks. With expert support and a proactive approach, we kept your business secure and resilient.
Cybersecurity
Multi-layered Cybersecurity solutions to safeguard your organisation’s digital assets
Centinell’s multi-layered cybersecurity solutions offer comprehensive protection against today’s cyber threats.
From employee training and advanced endpoint protection to secure cloud management, our services deliver a resilient shield for your organisation’s digital assets.

Cybersecurity Awareness
Empowering your team with Cybersecurity knowledge
Cybersecurity starts with your team. Centinell’s Training Awareness program equips your staff with the skills to recognise and respond to potential cyber threats, fostering a proactive security culture. Through regular training and hands-on learning, we help employees identify and avoid common risks, reducing the chance of human error.
Interactive Training Modules:
Continuous Updates:
Security-First Culture:
Duration: 1 day, 7 hours Location: Perth City
Delivery mode: Face-to-face workshop with access to online training materials for 6 months.
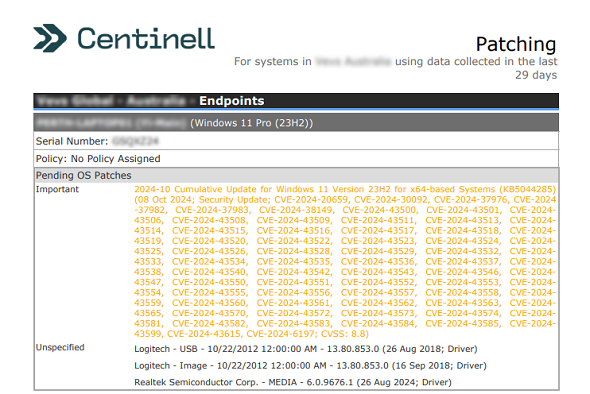
Patch Management
Keep Your Devices Software Up to Date
The Patch Management service keeps your systems current by regularly applying critical patches and updates to operating systems, applications, and devices. With our proactive approach, your IT environment remains secure and compliant, reducing vulnerabilities that cybercriminals can exploit.
This service is included in IT Managed Services: Centinell ServiceAlly and Centinell 365.
Automated Patch Deployment:
Vulnerability Management:
Compliance Assurance:
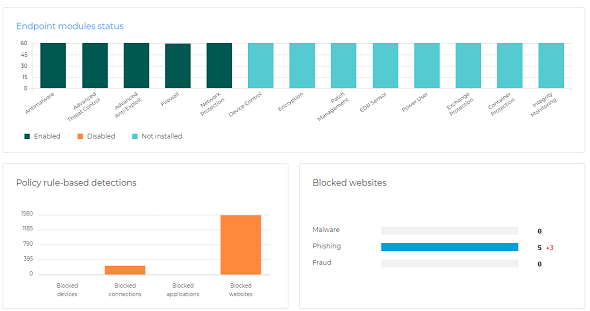
Endpoint Protection
Advanced Security for Devices
Centinell’s Endpoint Protection provides a robust defence for all devices within your organisation. With advanced detection and response capabilities, we shield endpoints from malware, ransomware, and other threats to ensure every device connected to your network remains secure.
This service is included in IT Managed Services: Centinell ServiceAlly and Centinell 365.
Real-Time Threat Detection:
Centralised Management:
Automated Threat Response:
Enterprise Multi-Factor Authentication (MFA)
Strengthen Security with Enterprise-Grade MFA
Enhance login security with Centinell’s Enterprise MFA, adding an extra layer of protection across all applications and devices. By requiring multi-factor authentication, we help prevent unauthorised access and reduce the risk of account compromise.
Strong Access Control:
Flexible Integration:
Enhanced Compliance:
Anti-Phishing & Spam Defense
Prevent Phishing and Spam
Centinell’s Anti-Phishing and Spam defence delivers powerful protection against phishing and spam threats. This AI-powered defence system stops malicious emails in their tracks, preventing phishing and other email-based attacks before they reach
your team.
Intelligent Threat Detection:
Real-Time Filtering:
Immediate Alerts:
Cloud Monitoring
24/7 Cloud security
The Cloud Monitoring service constantly monitors your cloud applications, detecting suspicious activity and potential breaches.
We help you maintain control and security across all your cloud environments by providing real-time alerts and detailed security insights.
Round-the-Clock Monitoring:
Instant Threat Detection:
Detailed Reporting:

Automated & Continuous SaaS Data Backup
Keep your devices software up to date
The Patch Management service keeps your systems current by regularly applying critical patches and updates to operating systems, applications, and devices. With our proactive approach, your IT environment remains secure and compliant, reducing vulnerabilities that cybercriminals can exploit.
This service is included in IT Managed Services: Centinell ServiceAlly and Centinell 365.
Automated Patch Deployment:
Vulnerability Management:
Compliance Assurance:
Tailored IT solutions: let's find the perfect fit for your business
Of course, we understand that IT services are not a one-size-fits-all. That's not a problem, let's talk for a specific solution for your business.
